7 Steps to Build a Human Firewall at Your Business
As highlighted recently on an episode of 60...
Responsive technical services to support your business and drive growth.
Industry leading security services to protect your company, data, and employees.
Leverage our team's deep experience to drive key business outcomes and transform your business.
Supercharge your productivity and drive collaboration for employees, clients, and vendors.
High performance cloud and network solutions to accelerate your business.
Industry leading security solutions to protect your company, data, and employees.
Embrace the modern cloud workplace and accelerate your business.

Join our team for our insightful
online and in-person events.
Dive into our growing content library and learn how we partner with clients to achieve success.
Learn how we partner with clients in key verticals to solve challenges and drive growth.
From the datacenter to the cloud, Sourcepass gets your high-performance projects done on time, on budget, and to your specifications to accelerate your business.
Follow our strategic approach that integrates technology, processes, and user engagement to optimize workflows and enhance overall organizational efficiency.
From servers, storage, and networking to IP video surveillance, access control, and structured cabling, Sourcepass gets your project done on time, on budget, and to your specifications.
Successfully implement IT security solutions with a comprehensive approach that combines robust technologies, proactive monitoring, employee awareness training, and risk advisory services to safeguard critical assets and mitigate potential risks.
Sourcepass follows a holistic approach with a customer-centric mindset to drive innovation, streamline operations, and deliver enhanced value in the digital age.

Sourcepass is structured to provide a dedicated team of both hands-on and virtual tech support and advisors no matter where you may be located.


And our local teams are backed by a deep bench of centralized services to round out incident response, risk advisory and 24x7 help as you need more.
![]()

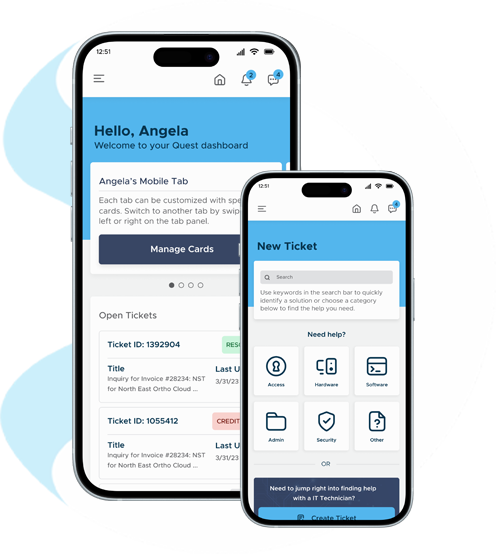
Whether simple or complex, your technology solutions will run seamlessly. You’ll have a real-time dashboard that provides fast and understandable information.


Our Quest platform allows you to perform frequent self-service tasks like adding a new employee to the network or ordering equipment.
![]()

We have an in-house and available 24/7/365 help desk for your immediate needs. But being always on doesn’t stop there. It’s a full-staff mindset.


Our partnerships include strategic advisors and technical leads, frequent and steady check-ins, and any-time access to our online Quest platform.
![]()

You’re handing us the “keys to the kingdom,” and you can’t afford for a partner to take that lightly. We will earn (and keep) your trust.


From materials procurement to cloud implementation and cybersecurity, our experts have earned compliance-level certifications and proved themselves throughout their careers time and again.
![]()

“Set-it and forget it” is not in our vocabulary. Our commitment to your business includes looking ahead to what’s next.


At the same time, our product innovation team is researching technologies, adding new capabilities and developing software-enabled products of our own. With the right technology, we unlock your potential for limitless growth.
![]()

Your business is unique, and IT solutions should be customized to meet real-time needs efficiently. Custom built, by us, for you.


Our teams focus on building software enabled solutions that leverage data analytics and process automation to deliver an exceptional digital experience as unique as your business.
![]()
“Sourcepass has always been quick to respond to us and has helped us tremendously over the years. When we decided to upgrade our technology, working with Sourcepass was a pleasure.”
“Sourcepass Infinity is able to provide the technical support that UTS needs, while maintaining a professional and pleasant working relationship. Jack and his team have been a pleasure to work with for many years.”
“The engineers that support us day-to-day are excellent and we are extremely happy with Sourcepass.”
"It is always a pleasure to be helped by anyone on the team there. Everyone is kind and cheerful while working to resolve the issues. Have not had one issue that was not fixed by your team. Thank you, you are greatly appreciated."
Sourcepass has been busy rolling out Microsoft...
Under the HIPAA security rules, certain...